Active Directory For Mac
With the move to cloud-hosted directory services, there is a common question that comes up relative to Azure® Active Directory®. That question is, “Can you authenticate Mac® devices against Azure Active Directory?” The more specific thought process is whether Azure AD can serve as the core identity provider for on-premises devices such as Macs.
Mac Active Directory Enrollment. Use your fully qualified domain name (FQDN). This is usually the same as your “Primary DNS Suffix” we got from our Windows machine. This allows us to get around any DNS configuration shenanigans. For the Active Directory settings put in the pre-Windows 2000 computer name from the above step. Domain password policies in Active Directory. At bind time (and at periodic intervals thereafter), macOS queries the Active Directory domain for the password policies. These policies are enforced for all network and mobile accounts on a Mac. But you're trying to adding your Mac to the active directory (sort of), not adding the directory to the Mac, I think? They would be two completely different things, and the latter I'm not sure is possible, which leads to more questions I'll post as a comment to your OP. – kumowoon1025 Mar 20 '18 at 17:07.
The simple answer is, “No.”
Azure Active Directory Authenticates Inside Azure
Azure Active Directory was designed to be the authentication source for Azure and Microsoft 365™ users, with the ability to manage Windows® 10 devices as well (along with web SSO capabilities). Azure AD doesn’t connect directly to devices that are on-premises or directly with other cloud infrastructure providers such as AWS®. Azure AD is primarily used within Azure and also when Microsoft Active Directory is present.
Active Directory Tools For Mac
Microsoft® designed Azure AD to be an adjunct to the on-premises Active Directory identity provider. In Microsoft’s model, identities are stored in the core, authoritative directory service located on-premises. AD and Azure AD connect in order for the identities to be used in Azure. This model makes the most sense for large organizations that have AD on-prem and also are likely all Microsoft Windows and Azure focused.
Limits of Storing Identities within Active Directory
Unfortunately, that model doesn’t work for many modern, cloud-forward organizations.
Almost all of these organizations have a mixed-platform environment. Many are leveraging G Suite or Microsoft 365 for their productivity platform. AWS or another cloud infrastructure is a part of their IT approach too.
And, perhaps most important, these organizations are opting to forgo Microsoft Active Directory altogether. No identity provider is on-prem, which belies the model Microsoft has articulated with Azure AD. As a result, organizations are forced to store identities within Azure Active Directory which works well for IT resources hosted at Azure.
Identities aren’t able to be exported to all third-party resources such as Mac and Linux machines; consequently, many on-prem systems struggle to authenticate with Azure AD.
Authenticating Macs Without Restrictions
There is another path that allows IT admins to not only leverage Azure but also authenticate their Macs and other non-Azure IT resources. Leveraging a core, cloud-based identity provider that can connect user identities to a wide variety of resources, including on-premises systems, cloud infrastructure, on-prem and SaaS applications, file servers, and WiFi is the better approach for modern, cloud-forward organizations.
JumpCloud’s directory service platform federates identities to Azure, G Suite, AWS, SSO solutions, and more. It’s an open platform that centralizes user management across the entire organization.
One identity is securely leveraged across the entire IT infrastructure.
One Directory To Rule Them All
If you are interested in authenticating Macs to Azure Active Directory, use JumpCloud’s identity management platform as your core identity provider in the cloud. Your Azure AD identities will be the same ones that your users leverage for their Macs.
Specifically, you can employ JumpCloud’s Apple MDM functionality to tightly manage and secure your Macs — even if they’re remote. As an IT pro, you will get full control over Mac user management and device management while still being able to leverage Azure, AWS, or Google Compute Engine™. You get to choose the best platforms for your organization but still have a single identity provider.
To learn more about how JumpCloud can support your desire to move to the cloud, drop us a note. In addition, give JumpCloud Free a try for yourself. Your first 10 users and 10 systems are free, with premium in-app chat support for your first 10 days.
Directory Utility User Guide
You use Directory Utility to add and configure advanced connections to directory servers. Your Mac accesses directory servers for user information and other administrative data stored in the directory domain of directory servers. Your Mac can connect to an Open Directory, Active Directory, or LDAP directory server.
When you add a directory server to (or delete one from) the Services list in Directory Utility, connection settings associated with that directory server are added to (or deleted from) the Authentication and Contacts lists. However, if you remove the associated connection settings from the Authentication and Contacts lists, the directory server is not removed from the Services list.
You can use the advanced features of Directory Utility to configure records, services, and search policies, and to configure a remote Mac that has macOS Server installed.
Os X Active Directory
The following are advanced features of Directory Utility:

Services: Configures a connection to directory servers (Open Directory, Active Directory, or LDAP) that users can access.
Search Policy: Configures where the Mac searches for user authentication and contact information.
Connect: Configures remote Mac computers with macOS Server installed.
Directory Editor: Configures record types and attributes in an authenticated directory domain or local directory.
Access an Open Directory domain
Configure a Mac to access a specific Open Directory domain. See Configure Open Directory access.
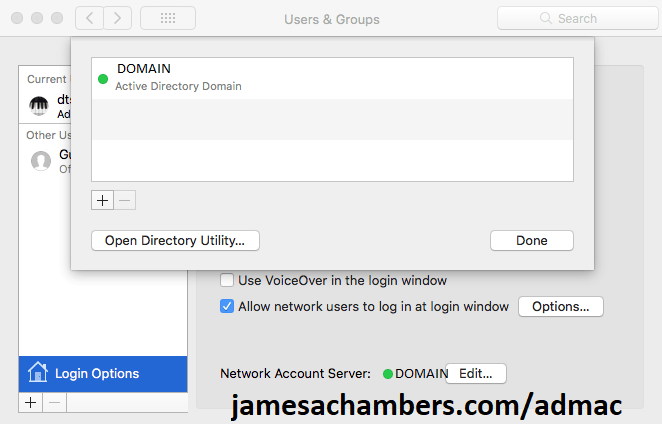
Access an Active Directory domain
Active Directory For Mac Download

Configure a Mac with macOS or macOS Server installed to access an Active Directory domain on a Windows 2000 or later server. See Configure domain access.
Access LDAP directories
Configure a Mac with macOS or macOS Server installed to access specific LDAP directories. See Configure LDAP directory access and Configure access to an LDAP directory manually.
